打log4j2补丁了?黑客有没有捷足先登?
攻击排查工具
log4j2 漏洞爆发,企业打补丁可能需要几小时到几天时间,但黑客攻击却只需要几分钟时间!到底是打补丁更快还是黑客攻击更快?如何确定自己的服务是否已经被攻击了?
为帮助广大企业自查是否遭到 log4j2 漏洞攻击,现提供一款检测工具及黑客攻击 IP 情报,用于检测服务器是否曾被 log4j2 漏洞利用攻击(注:但无法判定是否攻击成功),下载链接:https://static.threatbook.cn/tools/detect.py。若运行工具后发现告警提示,需要协助研判,请联系微步专业工程师协助您确认排查问题。电话:400-030-1051 转 3。
工具使用方式:
该工具为 python 脚本,在 python.2.7 及 3.8 的环境中测试通过。
命令行格式为:Python tools_py2_py2.py -p xxxxxx/logs,即 -p 后接的参数为需要扫描的 log 目录,默认扫描目录为 /var/log,建议用户扫描的目录有 [tomcat 日志目录 ($TOMCAT_HOME/logs),log4j2 应用日志目录 (log4j.properties 文件中 log4j.appender.*.File 的值),Redis 日志目录($REDIS_HOME/log),kafka($KAFKA_HOME/logs),Apache(/var/log/apache2),ES(/usr/share/elasticsearch/logs)]
使用示例如下:
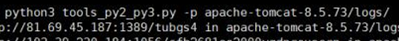
需要扫描的日志,包括但不限于:
- Struts2
- Apache Solr
- Apache Druid
- Apache Flink
- ElasticSearch
- Kafka
- Flume
- Dubbo
- Redis
- Logstash
工具原理:
匹配日志中的可疑字串(因此该工具仅支持明文日志检测,对于日志压缩等方式无法检测)
在野攻击排查示例
如下是我们对部署在公网中的蜜罐日志进行分析的示例:
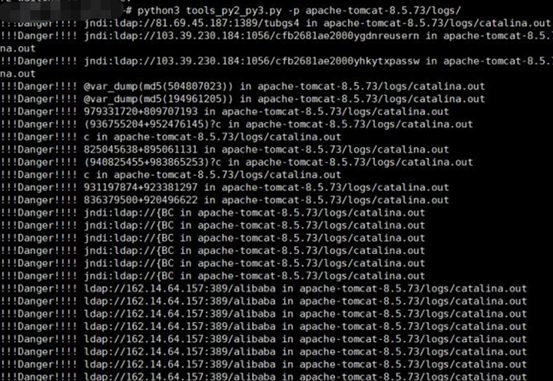
黑客利用log4j攻击IP情报
如下是我们捕获到的利用 log4j2 漏洞进行攻击的部分 IP 列表,有需要的用户可根据该列表进行自查:
104.244.72.115, 104.244.74.211, 104.244.74.57, 104.244.76.170, 107.189.1.160, 107.189.1.178, 107.189.12.135, 107.189.14.98, 109.237.96.124, 109.70.100.34, 116.24.67.213, 122.161.50.23, 131.153.4.122, 134.122.34.28, 137.184.102.82, 137.184.106.119, 142.93.34.250, 143.198.32.72, 143.198.45.117, 147.182.167.165, 147.182.169.254, 147.182.219.9, 151.115.60.113, 159.65.155.208, 159.65.58.66, 164.90.199.216, 167.71.13.196, 167.99.164.201, 167.99.172.213, 167.99.172.58, 171.25.193.20, 171.25.193.25, 171.25.193.77, 171.25.193.78, 178.62.79.49, 181.214.39.2, 18.27.197.252, 185.100.87.202, 185.100.87.41, 185.100.87.41, 185.107.47.171, 185.107.47.171, 185.129.61.1, 185.220.100.240, 185.220.100.241, 185.220.100.242, 185.220.100.243, 185.220.100.244, 185.220.100.245, 185.220.100.246, 185.220.100.247, 185.220.100.248, 185.220.100.249, 185.220.100.252, 185.220.100.253, 185.220.100.254, 185.220.100.255, 185.220.101.129, 185.220.101.134, 185.220.101.134, 185.220.101.138, 185.220.101.139, 185.220.101.141, 185.220.101.142, 185.220.101.143, 185.220.101.144, 185.220.101.145, 185.220.101.147, 185.220.101.148, 185.220.101.149, 185.220.101.153, 185.220.101.154, 185.220.101.154, 185.220.101.156, 185.220.101.157, 185.220.101.158, 185.220.101.160, 185.220.101.161, 185.220.101.163, 185.220.101.168, 185.220.101.169, 185.220.101.171, 185.220.101.172, 185.220.101.175, 185.220.101.177, 185.220.101.179, 185.220.101.180, 185.220.101.181, 185.220.101.182, 185.220.101.185, 185.220.101.186, 185.220.101.189, 185.220.101.191, 185.220.101.33, 185.220.101.34, 185.220.101.35, 185.220.101.36, 185.220.101.37, 185.220.101.41, 185.220.101.42, 185.220.101.43, 185.220.101.45, 185.220.101.46, 185.220.101.49, 185.220.101.54, 185.220.101.55, 185.220.101.56, 185.220.101.57, 185.220.101.61, 185.220.101.61, 185.220.102.242, 185.220.102.249, 185.220.102.8, 185.38.175.132, 185.83.214.69, 188.166.122.43, 188.166.48.55, 188.166.92.228, 193.189.100.195, 193.189.100.203, 193.218.118.183, 193.218.118.231, 193.31.24.154, 194.48.199.78, 195.176.3.24, 195.19.192.26, 195.254.135.76, 198.98.51.189, 199.195.250.77, 204.8.156.142, 205.185.117.149, 20.71.156.146, 209.127.17.242, 209.141.41.103, 2.10.206.71, 212.193.57.225, 217.163.23.58, 23.129.64.131, 23.129.64.131, 23.129.64.141, 23.129.64.146, 23.129.64.148, 45.12.134.108, 45.137.21.9, 45.153.160.131, 45.153.160.138, 45.155.205.233, 46.166.139.111, 46.182.21.248, 51.15.43.205, 51.255.106.85, 54.173.99.121, 62.102.148.69, 62.76.41.46, 68.183.198.247, 68.183.44.143, 72.223.168.73, 81.17.18.60, 88.80.20.86